Which of the Following Best Depicts a Phishing Scheme
Vulnerabilities can be weaknesses in either the hardware itself or the software that runs on the hardware. Hemp Russet Mites unlike spider mite.

Sniff Phish A Novel Framework For Resource Intensive Computation In Cloud To Detect Email Scam M 2019 Transactions On Emerging Telecommunications Technologies Wiley Online Library
She is a fearless loving playful little kitten.
. Get 247 customer support help when you place a homework help service order with us. A Cassandra writes a fictional column about the university she works for in an attempt to hurt enrollment after failing to earn tenure. At the 74th Academy Awards the film was nominated for 13 awards winning four.
0 1 2 1 2. It is a sensitive social engineering attack to gain access to the user credentials like passwords credit card details by masquerading oneself as a trusted body. Which of the following best depicts a phishing scheme.
Best Cinematography Best Makeup Best Original Score and Best. We notice you are outside the United Kingdom. AlcreatesGEN-483GAPHow To Make Roblox VIP Server Linkcomingsoonroblox phishingroblox phishing 2022roblox fake You can simply use DummyAPI as a free image API including metadata for every image.
This group of writers have passed strict English tests plus tests from their fields of specialization. Theorem 4 If we use decentralized anomaly detection to control the sensor false positive rate p 0 and if we use a conservative estimated ROC curve p 0 p 1 then Algorithm 1 chooses an operating point p 0 to maximize a lower bound on the true detection performance that is P D p 0 P D p 0. B Jennifer spreads negative information about a company online in an attempt to draw down stock prices for her colleagues.
We summarize our analysis in the following theorem. Perform unauthorized actions within a computer system. Thats why we take the recruitment process seriously to have a.
We understand that you expect our writers and editors to do the job no matter how difficult they are. Prevention is the best medicine. Because of this we do not allow traffic to our website from outside the UK so unfortunately you will.
But what they have in common is their high level of language skills and academic writing skills. Vulnerabilities are flaws in a computer system that weakens the overall security of the devicesystem. Do I need it at all and is there a Unity Captcha is a gem that use two levels of Captcha.
In particular we develop the backend Unity scripts in the 2D CAPTCHA control module in Fig. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. Examples of plants that do not press well and will Resin is a great way to preserve different things.
Vulnerabilities can be exploited by a threat actor such as an attacker to cross privilege boundaries ie. Best Customer Support Service. This means they recently joined the team.
In this attack the intruder injects a malicious code to manipulate the authentic data of the authorized user 2145. Best available This refers to a group of writers who are good at academic writing have great writing skills but are new in our team of writers. He was born August 7 1939 in Waterville the son of Arthur Check out our rope unity ceremony selection for the very best in unique or custom handmade pieces from our party decor shops.
According to a news release on Sunday One of my forms has a captcha. At the moment we only ship our products to addresses in the UK. Phishing is a fraudulent attempt usually made through email phone calls SMS etc seeking your personal and confidential information.

How To Avoid Highly Sophisticated Phishing Scams Affinity Technology Partners
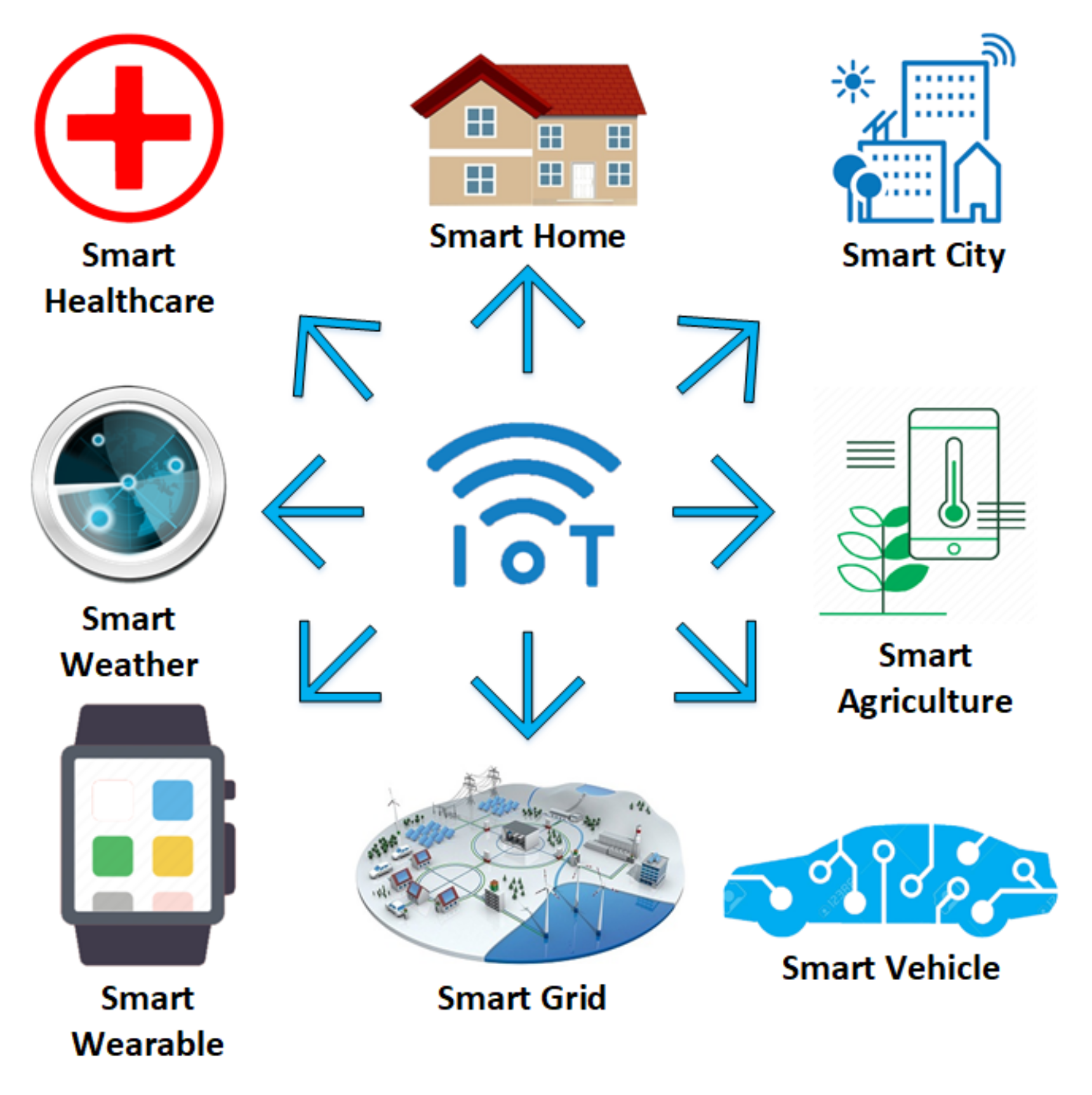
Sensors Free Full Text Identifying And Mitigating Phishing Attack Threats In Iot Use Cases Using A Threat Modelling Approach Html
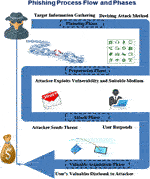
Frontiers Phishing Attacks A Recent Comprehensive Study And A New Anatomy Computer Science
No comments for "Which of the Following Best Depicts a Phishing Scheme"
Post a Comment